Top cybersecurity KPIs to track for risk mitigation

Published 2023-02-13
Summary - Learn about KPIs that help prevent cyber attacks
Cyber attacks and hacking are still big threats to small businesses and large corporations. Hackers have evolved from being lone individuals looking to break into corporate data for fun or fame. Now, companies must protect themselves from organized crime groups who use ransomware attacks to steal valuable customer and corporate data.
The FBI receives more than 900 reports to its Internet Crime Complaint Center every day. The agency reports that corporations across the U.S. lost a staggering $2.7 billion in financial losses from internet crime last year alone.
If there’s any good news in all of this, it’s that cyber security is no longer something just the CIOs and IT professionals worry about. It’s got the attention in the C-Suite as CEOs realize the importance of proper security and the risks involved in failing to manage it. In fact, 81% of executives admit their companies have been compromised by cyber security over a 24-month period.
How KPIs Help You Monitor And Manage
Business leaders monitor Key Performance Indicators in all aspects of business. From overall performance to revenue generation to sales leads to process, KPIs help managers tell the story of what’s working and what needs attention.
Cybersecurity KPIs can help you mitigate your risks by continuously measuring your performance against your cyber security goals. The best KPIs will communicate internal cyber risk, and help everyone make informed decisions around what actions need to be taken.
KPI: Total Number Of Security Incidents
Measuring the total number of security incidents over defined time periods (traditionally 1 month and 1 year) can give you a baseline for comparison. This KPI is simple to calculate as it is just a raw count of the number of security incidents against all parts of your system. When you see increased activity, your threat level needs to rise.
The Federal Government tracks these numbers in detail as shown in this chart:
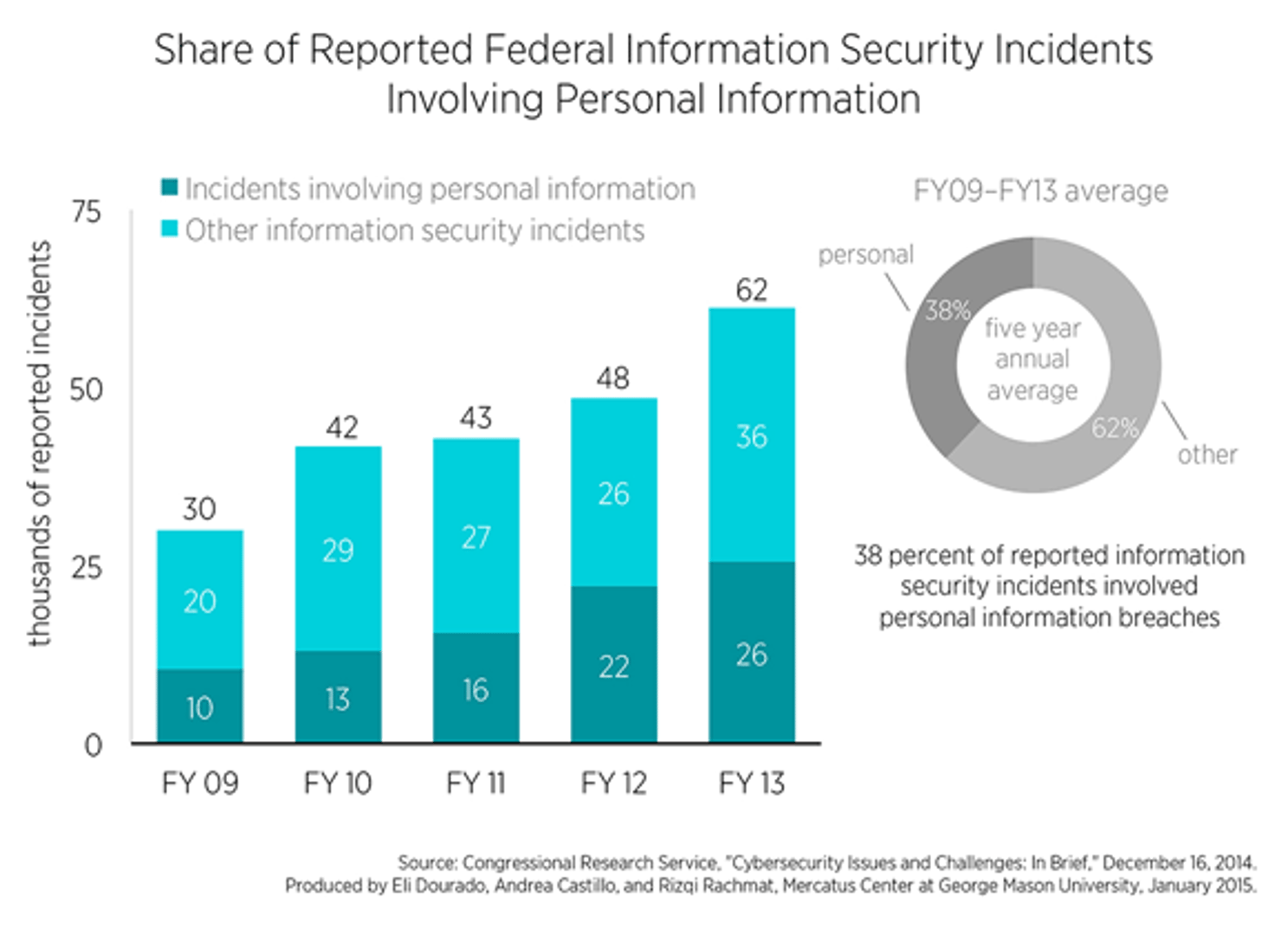
To get a great number, ensure you review data around phishing episodes, MitM attacks, but also security attacks against public facing we portals and any cloud data.
Once you have a sense of the number of security incidents per month or year, your team should work to maintain or lower that number. Automation can help identify significant threats for priority treatment. Artificially intelligent software can even spot trouble spots and isolate threats for further inspection.
It’s also important to track this KPI when implementing new procedures or tactics. Seeing a decrease or increase in the overall total number of security incidents can gauge the effectiveness of the new strategies.
KPI: Employee Interactions
With the significant increase in SaaS (Software as a Service), cloud-based services, and BYOD (Bring Your Own Device), the potential entry points for trouble have grown. Your networks and systems are vulnerable not just to security on your internal systems, but third-party connections and software outside immediate company control.
Monitoring employee interactions, remote connections, and cloud software can help you see potential threats. Calculate this number by having software count every time each employee accesses the network and how long they stay on the network. Ideally, have number that sums all employees and then one for each individual. This metric may indicate when an individual's account has been hacked and is being used for nefarious purposes.
To keep this number low and healthy, you need strong procedures and policies to govern connections with third-parties, BYOD devices, and cloud-based services. At the very least, make sure you are using encryptions, VPNs and private browsers for any remote connections to your network.
KPI: Mean Time To Identify (MTTI)/ Mean Time To Detect (MTTD)
Mean Time To Identify (MTTI), also known as Mean Time To Detect (MTTD) measures how long it takes to detect a breach. To calculate this KPI, count the days, or faction of days between the beginning of a system outage, service malfunction or other security issues and when the someone identifies the issue. The breach can be detected by the I.T. team, DevOps team or by an external source, in fact, 53% of breaches are reported discovered by an external source.
At large scale, this can be calculated by taking the sum of all the time incident detection times for a given technician or team and divide that by the number of incidents. In this calculation, it may be wise to remove outliers, such as catastrophic errors, to show a true average.
U.S. companies report an average of 206 days to detect a data breach. That’s a long time for threat actors to be inside your networks. The sooner you detect a breach, the more you can do to contain it.
KPI: Mean Time To Contain (MTTC)/ Mean Time to Resolve (MTTR)
Mean Time To Contain (MMTC), also known as Mean Time to Resolve (MTTR) tracks the amount of time it takes to contain a breach once it’s been identified. This is the count of days between identifying that there is a security issues, and when the fix is rolled out.
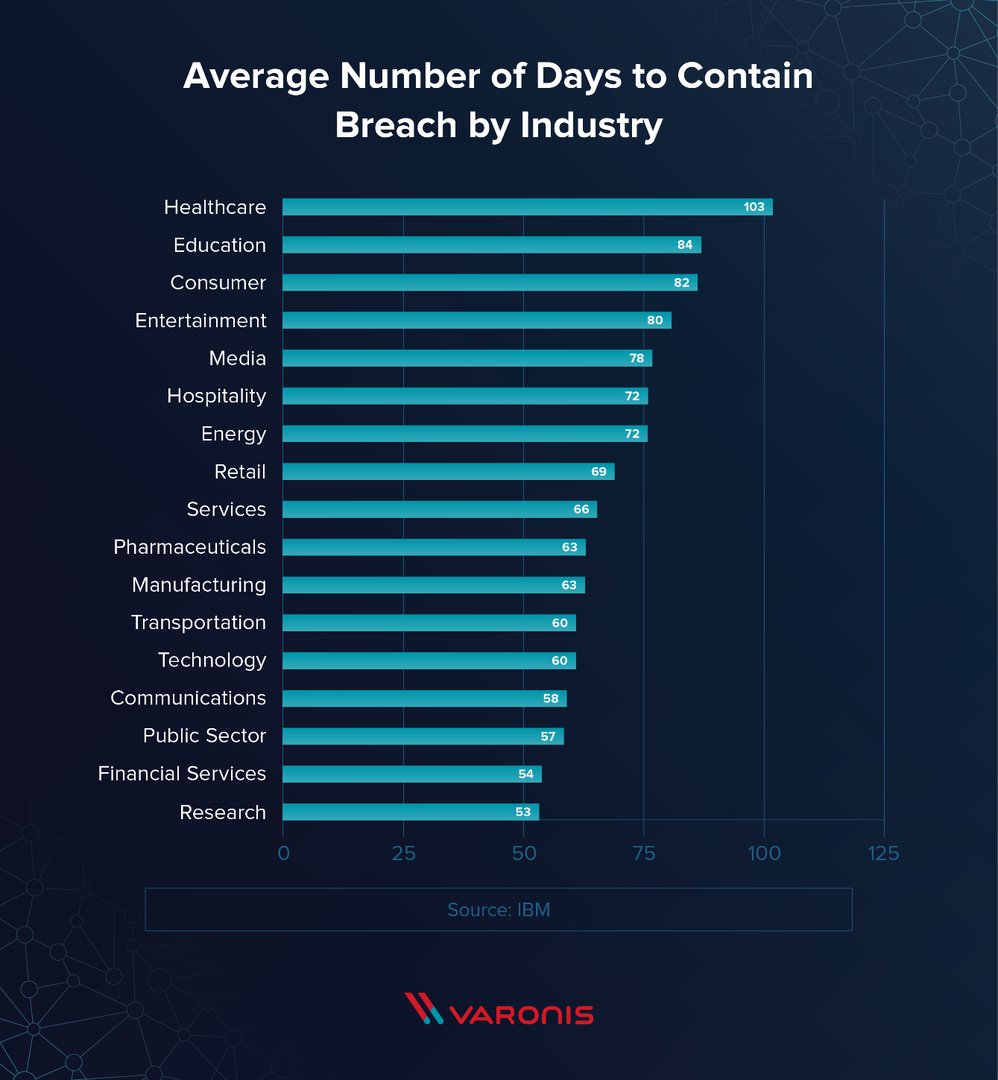
It takes companies an average of 55 additional days to contain a breach once identified both other organizations see this number rise to 208 days. High KPIs for both MTTI and MTTC can balloon security costs. These are two of the most important KPIs in measuring if your organization has the proper security information tools in place. Additionally, these two KPIs are metrics that all members of the security team can rally around and work to improve.
KPI: Cost Per Incident
The latest research shows the cost of a breach is a startling average of $8.83 million per incident. Costs go well beyond the technical aspects. Lost revenue, lost company reputation, public notices, employee time, and indirect costs add up quickly.
To truly track the Cost Per Incident of your organization, try to correctly bring in all resources, both human and technical, that were required to find the thread and fix it. This should also include missed revenue in terms of actual loss and potential loss. To calculate this KPI, add in three specific categories. Direct costs, such as actual forensic and investigative costs should be added to indirect costs like recovery time and costs to communicate the breach out. Finally, add in the lost opportunity.
This KPI is important to measure to continue to justify spend against preventive measure and show how painful weak I.T. can be.
KPI: Uptime/Downtime
Uptime and downtime simply refer to how often your site or software is working (uptime) or not (downtime). This is traditionally reflected in a percentage and the two should equal 100%. For example, 97% uptime means your website was working for 97% of the given time (usually a month) and your software had a 3% downtime for either software updates or because of an attack.
Every time you have to take something offline to patch security, you’re taking away an important tool for your organization or for your client. Tracking downtime due to security concerns can also help make the case for additional measures when it comes to budget time. In addition to hard costs, there’s lost productivity and potentially lost revenue.
KPI: Compliance
In many industries, there are compliance regulations that must be met. These are traditionally 3rd-party ratings given to the company after a review. Each industry security rating can be different and represented on a 0-10 scale, or A-F rating. Not only is it important to track any incidents that occur, but you may also be required to record your compliance and the steps you have taken to comply.
You may have to demonstrate that your systems meet industry standards are specific compliance regulations.
Justify The Cost Of Proactive Cybersecurity
Setting up KPIs is one of the best ways to quantify and identify problems in your systems to mitigate security risks. They can signal where you need to act and help justify the cost of proactive cyber security.
Author bio:
Matt Shealy is the President of ChamberofCommerce.com. Chamber specializes in helping small businesses grow their business on the web while facilitating the connectivity between local businesses and more than 7,000 Chambers of Commerce worldwide. Matt contributes to a number of business publications across the web such as Business.com and SAP.com.
Related Articles

The Hidden Value of SaaS Sign Up Rate Benchmarks
By Priyaanka Arora — January 10th, 2026
Klipfolio Partner How-To #1: Duplicating dashboards across client accounts
By Stef Reid — November 27th, 2025
Klipfolio Partner How-To #2: Company Properties can simplify client set-up
By Stef Reid — November 26th, 2025